A day in the life
PETER PARKER
Web Application Security Analyst
See how Peter orchestrates a strategic response to an emergent security threat - a new authentication bypass vulnerability - by utilizing the powerful capabilities of Qualys WAS and securing a vast web application landscape of 2000+ web apps.
1.A New Day, A New Threat
While enjoying his morning coffee, Peter learns about a breaking news of a critical authentication bypass vulnerability. He quickly logs into Qualys WAS to find a notification already there about a newly released QID designed to detect this exact threat that could allow attackers to access restricted resources without credentials. Recognizing the immediate risk to his organization's extensive web app portfolio of 2000+ web apps, he gears up to run an assessment across the network.
2.Swift Scanning Strategy
Without delay, Peter sets up a targeted scan in Qualys WAS for all applications, creating an option profile with the QID for the vulnerability. His goal: a thorough scan to identify any application that might be compromised by this new, critical threat.
3.Sensitive Data Exposure Prioritization
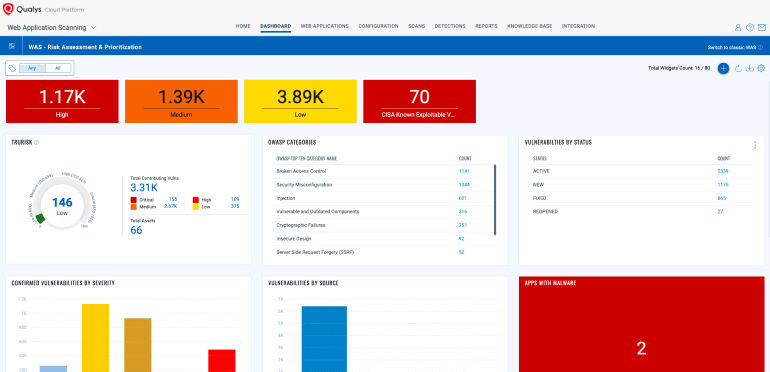
Peter understands that the risk is amplified by high-priority targets like web apps handling sensitive data, including Personally Identifiable Information (PII). He identifies these web applications from historical sensitive data exposure scan results and plans a targeted response strategy for these vulnerable points first, ensuring protection where it's most critical.
4.Critical Web Applications Dashboard
On completion of the targeted scans, Peter quickly creates a dashboard, categorizing web applications impacted by the new vulnerability, distinguishing between those with and without sensitive data, with the help of historical sensitive data exposure scan results. This dashboard allows Peter to prioritize remediation efforts targeting the most critical web applications first.
5.Critical Communication & Reporting
With insights in hand, Peter informs the CISO and security managers via a detailed email dashboard report. With the help of this immediate critical communication, the security team had clarity on the vulnerable apps and the steps needed to remediate the security threat.
6.DevOps Integration for Remediation
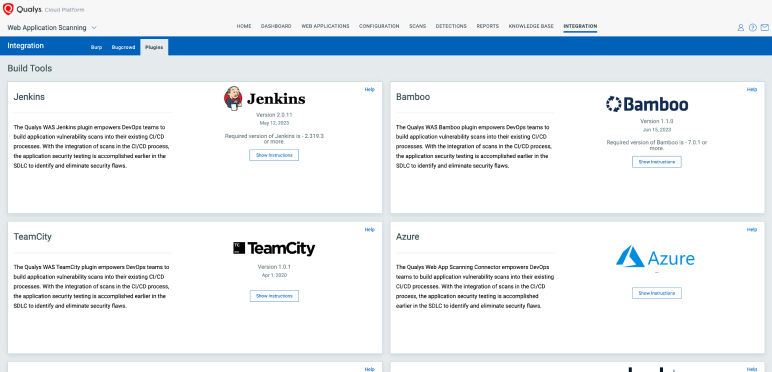
Peter uses existing integration of Jira and Qualys WAS to create tickets for impacted applications, providing the development teams with vulnerability details, impact assessments, and remediation steps. His actions ensures that the security fixes are set into motion promptly.
7.Secured Web Apps with Speed & Accuracy
Once the security fixes are complete, Peter conducts a thorough re-scan to confirm all issues have been resolved, effectively closing the loop. He notices that Qualys WAS has automatically added the vulnerability QID into the scanning schedules and option profiles for future scans. Content with the day’s successful outcomes, Peter logs off, looking forward to unwinding with his family over dinner, reassured that the organization's digital assets are secure with Qualys WAS.
A New Day, A New Threat
While enjoying his morning coffee, Peter learns about a breaking news of a critical authentication bypass vulnerability. He quickly logs into Qualys WAS to find a notification already there about a newly released QID designed to detect this exact threat that could allow attackers to access restricted resources without credentials. Recognizing the immediate risk to his organization's extensive web app portfolio of 2000+ web apps, he gears up to run an assessment across the network.
Swift Scanning Strategy
Without delay, Peter sets up a targeted scan in Qualys WAS for all applications, creating an option profile with the QID for the vulnerability. His goal: a thorough scan to identify any application that might be compromised by this new, critical threat.
Sensitive Data Exposure Prioritization
Peter understands that the risk is amplified by high-priority targets like web apps handling sensitive data, including Personally Identifiable Information (PII). He identifies these web applications from historical sensitive data exposure scan results and plans a targeted response strategy for these vulnerable points first, ensuring protection where it's most critical.
Critical Web Applications Dashboard
On completion of the targeted scans, Peter quickly creates a dashboard, categorizing web applications impacted by the new vulnerability, distinguishing between those with and without sensitive data, with the help of historical sensitive data exposure scan results. This dashboard allows Peter to prioritize remediation efforts targeting the most critical web applications first.
Critical Communication & Reporting
With insights in hand, Peter informs the CISO and security managers via a detailed email dashboard report. With the help of this immediate critical communication, the security team had clarity on the vulnerable apps and the steps needed to remediate the security threat.
DevOps Integration for Remediation
Peter uses existing integration of Jira and Qualys WAS to create tickets for impacted applications, providing the development teams with vulnerability details, impact assessments, and remediation steps. His actions ensures that the security fixes are set into motion promptly.
Secured Web Apps with Speed & Accuracy
Once the security fixes are complete, Peter conducts a thorough re-scan to confirm all issues have been resolved, effectively closing the loop. He notices that Qualys WAS has automatically added the vulnerability QID into the scanning schedules and option profiles for future scans. Content with the day’s successful outcomes, Peter logs off, looking forward to unwinding with his family over dinner, reassured that the organization's digital assets are secure with Qualys WAS.