Brinqa is a leading provider of unified risk management – enabling stakeholders, governance organizations, and infrastructure and security teams to effectively manage technology risk at the speed of business. Brinqa software and cloud services leverage an organization’s existing investment in systems, security, and governance programs to identify, measure, manage and monitor risk. With Brinqa, organizations are reducing response time to emerging threats, impact to business, and technology risk and compliance costs by over 50% through real-time risk analytics, automated risk assessments, prioritized remediation, actionable insights and improved communication. For more information, visit brinqa.com.
The integrated solution combines correlation of vulnerabilities, threat intelligence and business context with risk analysis and scoring to prioritize remediation efforts and measure program effectiveness.
Brinqa's flagship Risk Platform integrates with Qualys Vulnerability Management (VM) to deliver the most comprehensive way to analyze, prioritize and remediate vulnerabilities. Protect your organization against emerging threats and an ever-changing attacker landscape with a risk-based approach to vulnerability management.
The combined solution uses integrated asset management as the foundation for business-centric risk analysis of vulnerabilities. Scan data from Qualys is automatically imported and enriched with threat intelligence (e.g., iSIGHT Partners, Verisign iDefense, AlienVault OTX, IBM XForce). Enhanced vulnerability data is then analyzed with business context to evaluate real-world impact and immediacy of threats. Integrated workflows provide a highly simplified path to vulnerability remediation. Actionable, task-centric dashboards and reports ensure that there is a constant emphasis on undertaking actions with the greatest positive impact on the organization’s security posture.
Identify the Most Critical Threats to Your Business
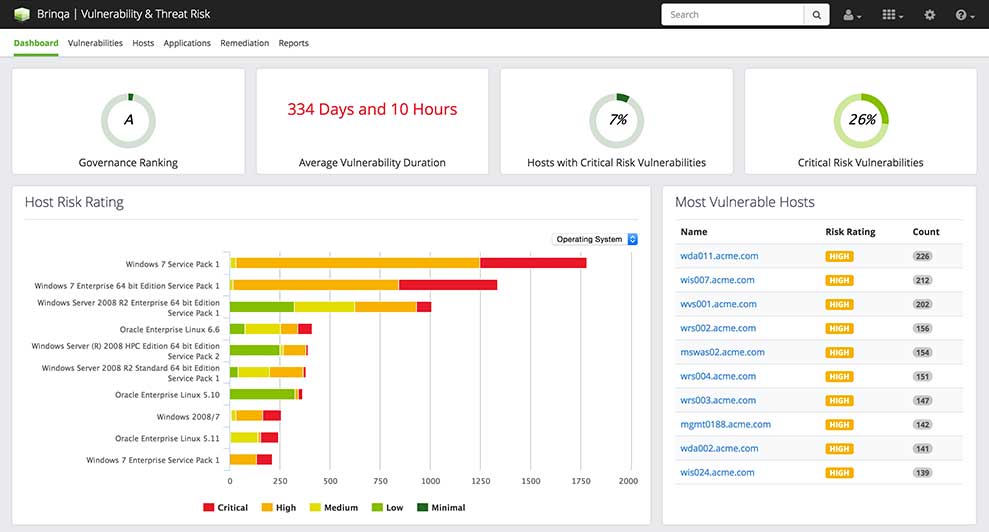
Security teams that function in isolation from the business they support run the risk of spending valuable time, money and human resource in addressing seemingly critical problems that may have minimal impact to business. The integrated solution puts an emphasis on representing goals, mandates and composition of the business being evaluated and factoring in this information during risk analysis. This encourages identification and resolution of threats that have the most significant impact to business.
Evaluate and Address Threats in Near Real Time
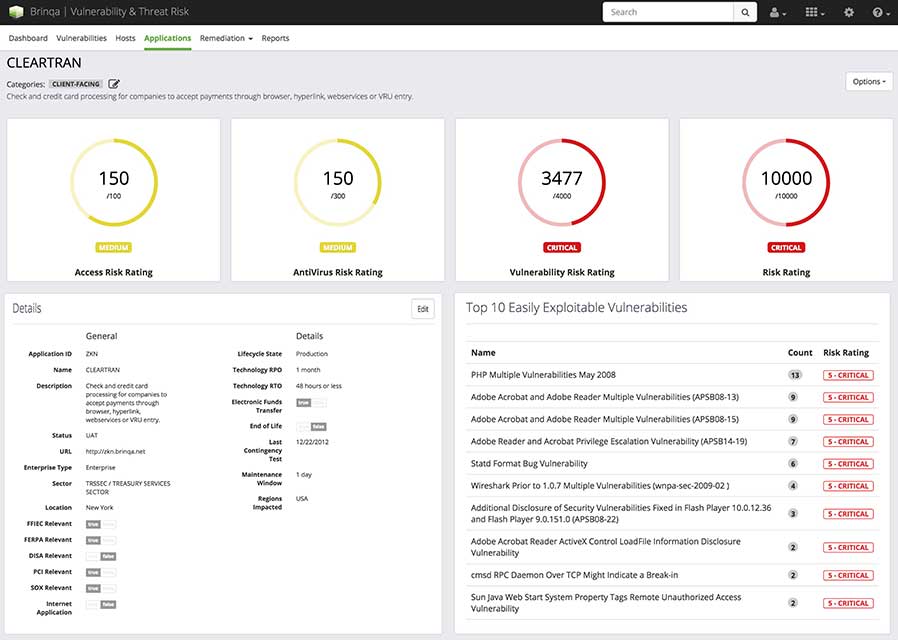
The vulnerability and threat landscape is constantly changing with new exploits, malwares and patches introduced every day. The integrated solution automatically incorporates numerous sources such as exploit databases and threat intelligence feeds, on a continuous basis, to evaluate the vulnerability posture of the organization in light of the most recent breach developments. These criteria are factored into the Brinqa vulnerability risk-rating model.
Collect, Correlate and Analyze
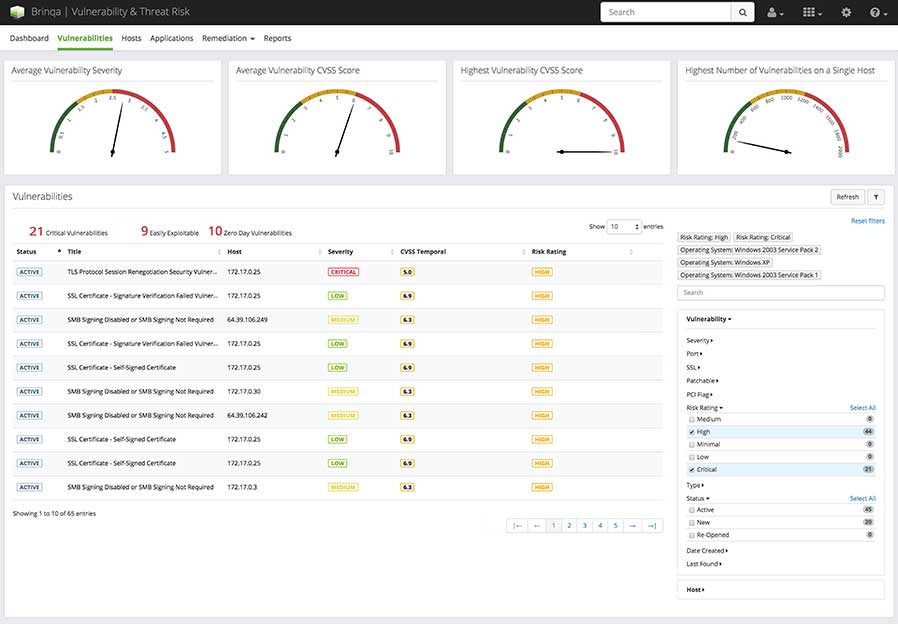
One of the most significant challenges faced by security teams today is the sheer volume of data being monitored and evaluated at any given time. With the exponentially growing magnitude of data, the mechanisms to query, splice, analyze and represent this data become increasingly important. The solution provides mechanisms such as free text search, contextual search, advanced filtering and more for security professionals to easily locate and identify relevant information.
Encourage Effective Remediation
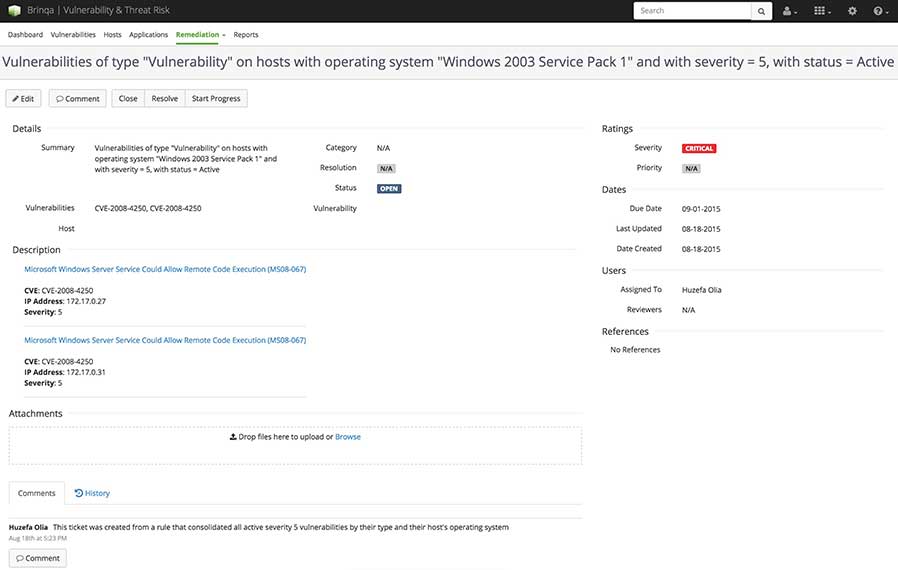
A critical goal of efficient vulnerability management is to facilitate the remediation of prioritized threats. Advanced vulnerability grouping for ticket consolidation, built-in Brinqa workflows and integration with common IT service management systems (e.g., ServiceNow, JIRA, etc.) provide an easy path from identification and prioritization to remediation. Integration with vulnerability definition, classification and intelligence frameworks provides useful instruction about how to remediate vulnerabilities. Closed-loop validation ensures that remediation efforts are tested and evaluated accurately.
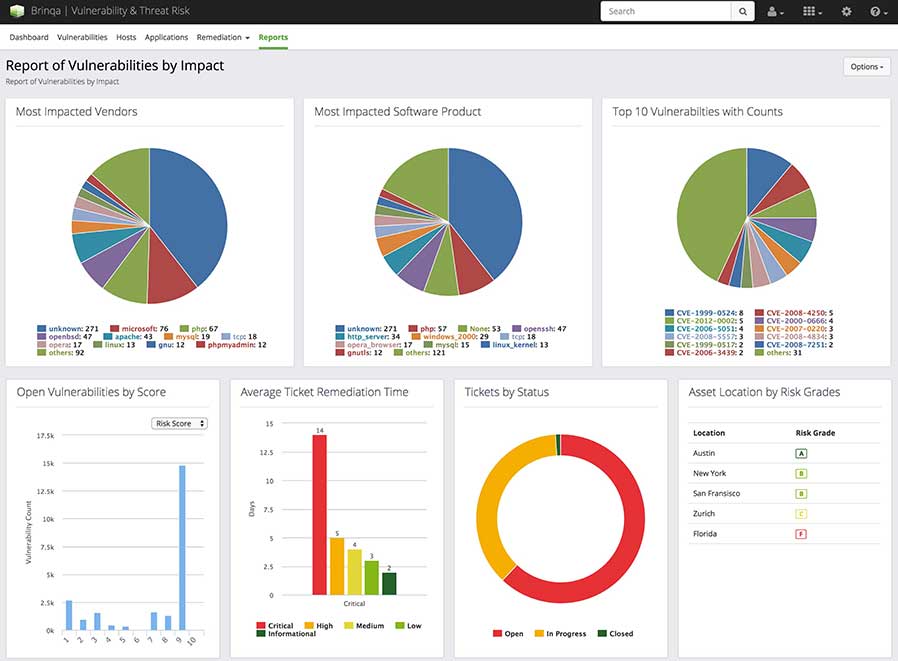
Communicate, Collaborate and Transform Your Business
Visual graphs provide a unique perspective for understanding security data and deriving insights through advanced analytical processes like graph-clustering and node-classification. The integrated solution provides a comprehensive reports catalog targeted for a wide audience range, from network administrators to security teams and C-level executives, to ensure that stakeholders at every layer of the organization are effectively informed and actively engaged in the decision-making process.
How It Works
The integrated solution comes with ready-to-use risk models, asset hierarchies and report templates. Users can configure the turn-key solution to automatically collect scan results for advanced consolidation, correlation and risk scoring of vulnerabilities to deliver immediate risk insights to stakeholders.
The risk-scoring model augments vulnerability classification and characteristics with additional sources such as internal and external exploit data and threat intelligence. Vulnerabilities may be consolidated based on type and asset ownership rules to provide near real-time visibility, through pre-configured dashboards and reports, to reveal the most critical and imminent threats to the business. Built-in integrated workflows provide a simple, guided path to efficient closed- loop remediation.
More information about Brinqa can be found at brinqa.com.
